Winlogbeat setup in windows
What is Winlogbeat
- Winlogbeat is an agent that ships windows event logs continuously to Elasticsearch
- Winlogbeat runs as a windows background service
- Winlogbeat can be configured with a .yml file to control what logs are sent to Elasticsearch

About windows event logs
- Windows event logs are the records of events generated by the windows operating system
- Windows event logs can be used by administrators and security professionals to investigate about the security threats, performance issues, errors in the Windows operating system
Types of Windows event logs
Windows event logs can be of types Security, System, Setup and Application
- Security logs - related to system safety. Example: Login attempts, object access etc.
- System logs - related to system and its components. Example: startup, shutdown, system time changed etc.
- Setup logs - related to installation of windows OS components. Example - installation of windows update packages
- Application logs - related to software installed in the OS. Example - problem in loading a software (like firefox)
Attributes of a windows event log
- Level - information, critical, warning, error, verbose.
- Date and Time
- Source - Program or component that caused the event
- Event ID - number that specifies the event type
- Task category - Event log type
- User - Username of user logged onto the machine when the event occurred
- Computer - Name of the computer
Viewing Windows event logs
- Windows event logs can be viewed using the “Event viewer” application as shown below
- Windows event logs can be viewed in Event viewer, but complex logs filtering with queries or analyzing event logs is not easy

Install and run Winlogbeat
- Download Winlogbeat zip file from https://www.elastic.co/downloads/beats/winlogbeat
- Extract the zip file in
C:\Program Filesfolder - Open powershell as administrator in the winlogbeat folder and run the script
.\install-service-winlogbeat.ps1. If script execution is disabled in the system, try runningPowerShell.exe -ExecutionPolicy UnRestricted -File .\install-service-winlogbeat.ps1 - Now Winlogbeat is installed as a windows service. The windows service can be controlled from the “Services” windows application
- Winlogbeat service logs can be seen at the location
C:\ProgramData\winlogbeat\logs. This can be useful to debug when Winlogbeat service is not running. - Before starting the service, configure Winlogbeat with
winlogbeat.ymlfile
Configure Winlogbeat
- Winlogbeat can be configured using
winlogbeat.ymlpresent in the winlogbeat installation folder. Restart Winlogbeat service after changing winlogbeat.yml file for changes to take effect.
Configure Elasticsearch connectivity
- Elasticsearch URL and credentials can be specified in the
output.elasticsearchsection of winlogbeat.yml file as shown below
output.elasticsearch:
# Array of hosts to connect to.
hosts: ["localhost:9200"]
# Protocol - either `http` (default) or `https`.
protocol: "http"
# Authentication - either API key or username/password.
#api_key: "id:api_key"
username: "elastic"
password: "changeme"
Configure windows event logs to be shipped
- An example configuration in the
winlogbeat.event_logssection of winlogbeat.yml file can be seen below. All configuration options can be found at https://www.elastic.co/guide/en/beats/winlogbeat/current/configuration-winlogbeat-options.html
winlogbeat.event_logs:
- name: Application
ignore_older: 72h
- name: System
- name: Security
event_id: 4624, 4625, 4700-4800, -4735
level: critical, error, warning
- name: Microsoft-Windows-Sysmon/Operational
- name: ForwardedEvents
tags: [forwarded]
- The name of the desired log can be specified using “name” field. To know the name of the log in event viewer, right click on the log in the left pane and view properties as shown below
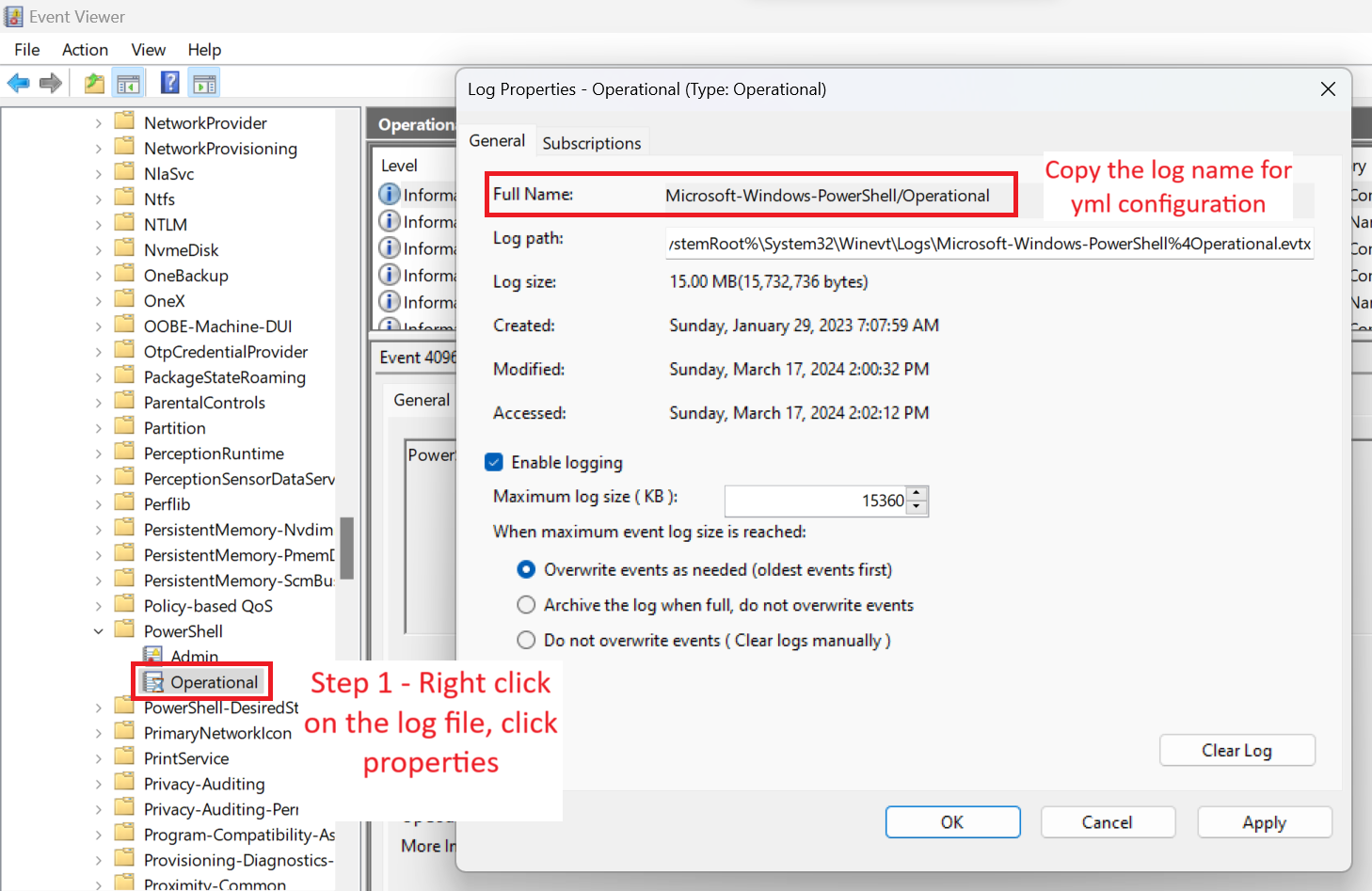
ignore_olderattribute can be used to ignore logs older than specified time. This helps to avoid unnecessary old logs while running Winlogbeat for the first timeevent_idattribute can be used to what specific event ids are to be included or excluded. For example4624, 4700-4800, -4735means, only event ids 4624 and event ids between 4700 and 4800 would be shipped but 4735 will not be shipped.levelattribute can be used to specify which log levels would be shippedtagsattribute can be used to mention a list of tags that will be attached to the logs while shipping. This can be useful to easily search logs in Elasticsearch
Load sample Kibana dashboards and index patterns
- Ensure
setup.dashboards.enabled: trueinwinlogbeat.ymlto load sample Winlogbeat dashboards in Kibana. Kibana connectivity can be configured in thesetup.kibanasection
View and query windows event logs in Kibana
- Open “Discover” page in Kibana.
- Select the index pattern / data view as winlogbeat-*. Create the index pattern / data view if not present
- Now all the raw windows logs can be seen as shown below

Kibana dashboards for Winlogbeat
- Go to the Dashboard page in Kibana
- Search for Winlogbeat. A sample Winlogbeat dashboard can be seen below

Video
The video for this post can be found here
References
- Winlogbeat configuration guide - https://www.elastic.co/guide/en/beats/winlogbeat/current/winlogbeat-installation-configuration.html
- Excellent explanation to each of windows security events - https://www.ultimatewindowssecurity.com/securitylog/encyclopedia/Default.aspx?catid=2&subcatid=8
- About windows event logs and terminology - https://www.solarwinds.com/resources/it-glossary/windows-event-log
Comments
Post a Comment